Is your WordPress password secure?

Passwords remain one of the most important defences against private or confidential information being made available to unauthorised users
GovPress is dxw’s WordPress platform for the public and charity sectors and other clients with strict legal and regulatory requirements. Because our clients care about security, it has always been at the heart of what we do, although much of that work happens in the background. We’ve been quietly making incremental security improvements for our clients for more than a decade now. This post is about one of those small improvements we’ve recently made to how we handle passwords to help keep our clients safe.
Passwords matter
The Department for Digital, Culture, Media and Sport reported that 50% of businesses and 32% of charities had experienced some form of cyber security breach or attack in the last year. Over time, the number of cyber attacks have increased. The International Monetary Fund found they have doubled since the pandemic and the rise of artificial intelligence suggests that attackers will soon find new ways to target websites.
Despite Bill Gates predicting their demise 20 years ago, passwords remain one of the most important defences against private or confidential information being made available to unauthorised users. Good password management is a collaboration between users and system providers like dxw. Passwords need to be long, unique, random and securely stored. To address the last of these, back in 2011 we changed our WordPress sites to use bcrypt, a stronger encryption algorithm than the WordPress default. We still use bcrypt now (WordPress still uses MD5 for portability and backwards-compatibility reasons) and that change was just one of many we’ve made to improve the overall security of our sites. However, choosing a long, random and unique password is up to the user.
Nearly half the web is a big target
Good password management matters for every application and platform, but WordPress is a little different to other systems. WordPress sites make up over 40% of the web and over 60% of content management systems, a huge percentage and one of the selling points of the CMS. Having such a large market share means that it’s easy to find documentation on WordPress, hire a supplier or find add-ons (plugins) in the large ecosystem that has grown up around the software. The next most popular CMS is Shopify, with just 4.4% of all websites.
The downside of that popularity is that WordPress is a very common target for security scans and malicious attacks. When a site is scanned a large number of speculative visits are made to the site, usually by an automated system which can make thousands of requests very quickly. These might be gathering information about the site, attempting to login, or trying to exploit a bug or security hole in the site. Most security scans we see in practice are aimed at WordPress sites, including the scans we see on non-WordPress systems.
We have a number of ways to respond to security scans and malicious attacks and one of our most important is to block or challenge users who repeatedly fail to log in. However, names and email addresses can often be guessed from the content of websites, and our efforts will fail if users have passwords that can be guessed on the first few attempts.
Guessable passwords are easily hacked
If your username is admin and your password is 123456 then not only can your credentials be easily guessed, but your password appears on every list that bad actors use to try to login to public sites. In 2019 the password 123456 appeared over 23 million times on lists of regularly used credentials. You can probably guess a few of the other popular passwords, and the top football related password was liverpool (sorry Arsenal fans).
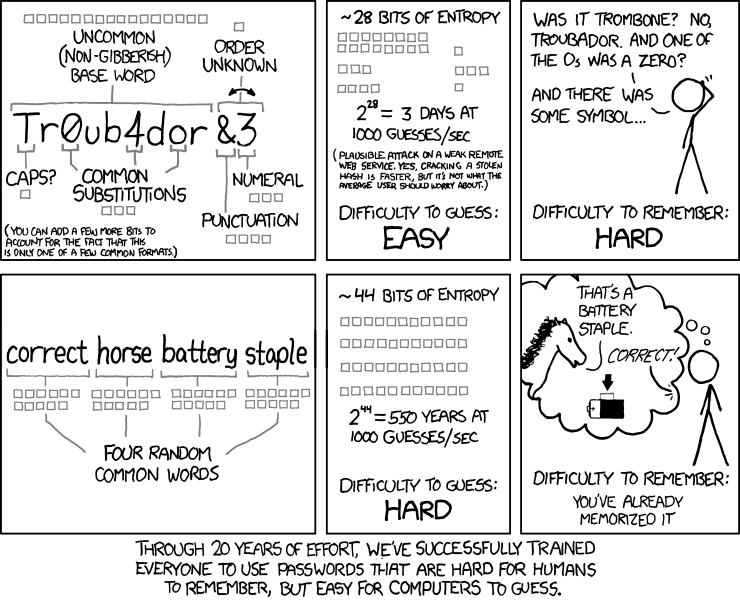
Comic showing passwords that are hard for humans to remember but easy for computers to guess
Password spraying and credential stuffing attacks are 2 forms of attack that involve attempting to login to websites. These attacks involve using commonly used or explicitly stolen credentials to attempt to gain unauthorised access to a user account.
Mitigating these attacks needs a two-pronged approach – on our side we need to block malicious attacks, but we also need our clients and end-users to pick strong passwords so that an attacker’s first few attempts at logging in are not successful.
Back in 2013 we started keeping a list of common passwords that we do not allow users to set on our WordPress sites to help users choose less guessable credentials. That list consists of passwords from lists produced by security researchers as well as ones we have seen in security scans and attempted attacks on the sites we host.
Expanding the banned password list
As part of our efforts to continuously improve our WordPress platform, we recently added the UK National Cyber Security Centre top 100,000 passwords to the unique credentials from our own banned passwords list.
The NCSC list is a subset of passwords gathered by Microsoft security researcher Troy Hunt from data leaked due to security breaches on public sites. Troy has made over 13 billion of these passwords available so that users can check their own passwords and hosting providers like dxw can give their users better advice about their credentials. NCSC research found that 75% of participating organisations had accounts with passwords in the top 1000 of Troy’s list and 87% had passwords in the top 10,000. This makes banning the top 100,000 passwords a good compromise between keeping users safe and keeping systems usable.
Help us to help you
To avoid password spraying and credential stuffing attacks yourself, you should make sure that your own passwords are as long as possible and ideally contain a variety of letters, numbers and symbols. If you can only act on one of those pieces of advice, make your password longer and if you need to be able to remember a password use a whole phrase rather than a word. Something similar to “correct horse battery staple” is good, but you should definitely not use that exact phrase!
These good practices are much easier if you use a password manager to store your credentials securely. Most apps on the market also have plugins for web browsers to automatically log you into sites where you have an account, which makes good security practices much easier to follow. It probably goes without saying, but you should never share passwords with anyone else or reuse passwords between sites or applications. If you are worried that one of your passwords might already have been compromised by a data leak or breach, you can go to https://haveibeenpwned.com/ and enter your email address to find out, and change any of your passwords that are reported there.
To be safer still, make use of two-factor authentication anywhere you can. This will require you to authenticate yourself via a second factor, such as a confirmation email or a code sent to an authenticator app or via an SMS message.
After nearly a decade and a half of developing, hosting and maintaining WordPress sites for diverse clients like the National Audit Office and the British Film Institute, we know that good security is not a target to be met but a process of continuous change to adapt to the developing technological landscape and the behaviour we see from attackers.
GovPress offers a managed service for clients who need WordPress sites and we work hard to make security something that users do not need to actively worry about, and this recent change is a small part of those efforts. If you are thinking about your site security, maybe you’d like to add two-factor authentication to your site or you just don’t know where to start, we’d love to chat to you. Please get in touch with us at contact@govpress.com.